
2019 End Of Year Report
A Letter from the Executive Director
As I write this introduction to our 2nd yearly report, in the chaos of 2020, I’m struck by how much our small society managed to accomplish in 2019, and how much work remains to be undertaken.
2019 saw us find critical issues in public infrastructure around the world , from Vancouver to Zürich. It also saw us continue our commitment to building the next generation of consent-enhanced software.
Our supporter base grew as more people see the need for societies like ours , agile research groups, intrinsically linked with the communities we work with and dedicated to building a future that doesn’t just include marginalized communities but it actively driven by them; us.
I want to again thank all of our supporters, institutional donors, volunteers and staff; Without you Open Privacy, and the vital work we do, could not (and would not) exist.
Our mission has only just begun, and I invite you to join us again as we continue to gain momentum and help build a better world.
Sarah Jamie Lewis
Executive Director, Open Privacy Research Society
Projects

Disclosure of Cryptographic Vulnerabilities impacting the Swiss Post / Scytl / iVote e-voting Systems
In March 2019 Sarah Jamie Lewis of the Open Privacy Research Society, along with Vanessa Teague (University of Melbourne), and Olivier Pereira (UCLouvain) published details of critical vulnerabilities impacting evoting systems in Switzerland and Australia. These vulnerabilities were soon confirmed by the vendor Scytl, resulting in an emergency patch being installed during an election in New South Wales, and a “temporary” suspension of evoting offerings by Swiss Post.
In June the Swiss Federal Council, citing these disclosures, delayed the introduction and evoting as an official option, and shortly after SwissPost announced that it would not be offering its system for use in the October federal elections (despite having offered it in previous elections).
Just as math can protect the speech of the marginalized from the powerful, it can also be used to prove to everyone that power is not working as it claims.
Speaking math to power works.
Open Privacy received a share of a bug bounty payment, 2500 Swiss Francs ($3400 CAD) from Swiss Post for disclosing these issues, donated by Sarah Jamie Lewis.
Disclosure of Vancouver Patient Medical Pager Data Breach
In November 2018, Open Privacy staff members discovered data from patients admitted to Vancouver area hopsitals was being broadcast unencrypted over paging systems, making them openly available to anyone in the Great Vancouver Area with minimal equipment and expertise.
The data being broadcast included the patients name, age, gender marker, diagnosis, attending doctor and room number. Other broadcasts regarding medical tests such as x-rays are often associated with a patients last name or medical number, making their progression through hospital systems trivial to piece together. We have been able to confirm the authenticity of this data by cross-referencing this data with a public obituary.
Open Privacy immediately began responsible disclosure of this issue with Vancouver Coastal Health. However, the disclosure was initially ignored, and it wasn’t until Open Privacy contacted members of the media, and the Office of the Information & Privacy Commissioner in B.C. that VCH began to investigate the breach.
News of the breach received coverage in Vancouver, and across Canada.
In September 2019, Vancouver Coastal Health announced that they had removed
the sensitive Diagnosis field from these broadcasts, but further concerns
were raised about how widespread such breaches of patient medical records
might be in Canada.
For more information regarding the timeline and detailed impact of this disclosure please see our project page.

Cwtch
Communications metadata is known to be exploited by various adversaries to undermine the security of systems, to track victims and to conduct large scale social network analysis to feed mass surveillance. Metadata resistant tools are in their infancy and research into the construction and user experience of such tools is lacking.
Cwtch began as an extension of the metadata resistant protocol Ricochet to support asynchronous, multi-peer group communications through the use of discardable, untrusted, anonymous infrastructure.
Cwtch aims to solve many of the problems faced by the marginalized communities that we serve but primarily it solves the anonymous-first-contact problem.
Many people in the communities we serve wish to build relationships with others in the community or people outside of their community, but they wish to preserve their privacy and minimize the risk of someone discovering information about them that they do not wish to share publicly.
Cwtch is designed to allow communities to build safe & secure spaces that can provide discussion platforms, advertisement services, shared lists.
At the end of our first year we released a prototype Cwtch app for desktop and Android. 2019 saw us continue development on Cwtch starting to mature and improve it in many ways.
The first half of the year saw a large investment in Android support and stability which involved sizable restructuring and refactoring of existing code. The end of the year was largely spent adding support for managing multiple profiles to Cwtch so that one user could easily, seamlessly and safely manage multiple profiles at the same time.
In addition, 2019 also saw Cwtch add Internationalization support and alpha translations for Portuguese, German and French.
As the year progressed we split off parts of the code base into reusable packages including a logging package and tor connectivity package that are now being integrated with other Open Privacy projects.
We rewrote our peer to peer connection code into more modular package called Tapir.
As we move into the 2020 financial year, we are most excited about the UX and UI improvements that are being driven by our new Staff Designer and the approaching Cwtch Beta.

OP:Sec
OP:Sec, our program to disseminate free security and privacy programming to our community, continued apace in 2019. Our embedded staff member conducted dozens of one-on-one consultations, group seminars, and even direct IT support on a weekly basis to queer folks and sex workers.
In one particularly notable instance, Open Privacy was brought in to help respond to an instance of white supremacist harassment of an advocacy & support organization. Our OP:Sec staff member assisted with shoring up organizational security, provided an all-hands seminar on personal digital hygiene practices, and followed up with individual consultations for at-risk or concerned staff members.
We also began planning to increase availability and systematize OP:Sec. However, finding a suitable funding source for this type of work and audience remains challenging. It is directly due to the generosity of our individual donors that we had the flexibility and independence to be able to continue this program into 2019 and achieve what we have so far.
On behalf of everyone helped for free by the OP:Sec program we thank you so much for this hugely impactful component of our work. <3
Donations and Support
Continuing the trend from our 2018 financial year, Open Privacy relied heavily on support from individual donors, rather than organizational or governmental grants in our 2019 financial year. The flexibility of this funding has allowed us to produce research that would be impossible to produce in other environments.
Open Privacy did receive one very large donation from an organizational donor, accounting for just under a third of total donation revenue.
Patreon
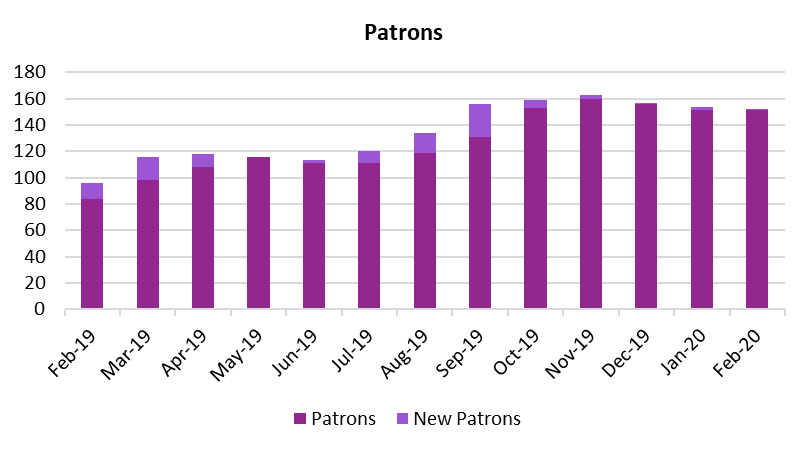
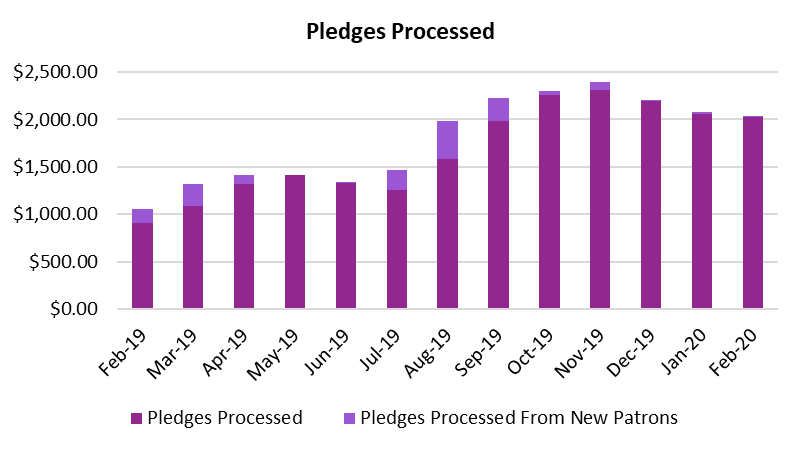
In the 2019 financial year we saw a net increase of 56 (a 58% increase from the 2018 financial year) new patrons . contributing a net monthly support increase of $980.64 (a 93% increase from the 2018 financial year).
Paypal
In the 2019 financial year we received approximately $18,800 CAD through Paypal donations.
Cryptocurrencies
We received approximately $76,000 CAD through cryptocurrency donations.
- Zcash: ~$54,600 CAD
- Bitcoin: ~$20,800 CAD
- Monero: ~$1,200 CAD
Cryptocurrency donations made up 44.57% of all donations in our 2019 financial year. Down in relative terms from 61.27% in 2018.
Grants
We received a generous donation of 1044.41369 ZEC ($40,000 USD) from the Zcash Foundation.
Benefit Events
There were no benefit events on behalf of Open Privacy in 2019.
As noted in our 2018 report, the proceeds from the event “Blockchains Against Evil” is reported in our 2019 financial year, despite it taking place in 2018.
Travel Assistance / Event Discounts
Open Privacy received travel assistance from Swiss Cyber Storm to attend the conference.
Organizational Structure
There were several major changes to the operations of Open Privacy in the 2019 financial year.
Reflecting our role and mission as a research organization, our largest expense in the 2019 financial year, accounting for over 85% all expenses was that of staff salaries: $92,217 CAD (up from $32,386 CAD - note that we only started paying staff members late in 2018).
In the 2019 financial year, both the Director of Engineering and Research Director received salary increases in line with our goal as stated in our 2018 financial report; to provide our staff with a living wage.
- Director of Engineering: 50% increase above B.C. Minimum Wage
- Research Director: 20% increase above B.C. Minimum Wage
We also created and hired our first non-director position, Staff Designer.
Finally, in December 2019, we committed to a small office in Vancouver. The cost of which will be $17,459.84 in the first year (through December 2020).
The Open Privacy Board of Directors
Open Privacy added 1 additional board member in the 2019 financial year , bringing the total number of directors to 8:
- Sarah Jamie Lewis - Chair (Executive Director)
- Erinn Atwater - Vice Chair (Research Director)
- Dan Ballard - Treasurer / Secretary (Director of Engineering)
- Norman Shamas - Director
- Yuan Stevens - Director
- Cynthia Khoo - Director
- Cecylia Bocovich - Advising Director
- Kit - Director







Financial Statements
As we did in 2018, the board gave the Executive Committee authority to commission a Notice to Reader engagement in line with the estimate of $2000 as provided by Smythe CPA.
A copy of the Notice to Reader can be found here. This does not constitute a formal audit of the Open Privacy Research Society.
The board did consider estimates for a formal audit, but the cost would have exceeded 10% of our income, and the board ultimately determined this would not have been a good use of funds. It is the goal of the Executive Committee, and the board, to engage in a formal audit once our funding levels are sufficient to support it.









